Scenario
I had a task to set up and configure Windows Intune. I needed to ensure that domain joined and NON domain joined Windows 10 systems could enroll in Windows Intune. So, I did what I always do and rigorously started researching the various steps required to get this solution set up.
I was more than a little surprised to find such an abundance of Microsoft articles and KB’s but I soon realized how incongruent they all were with regards to accomplishing the end goal; “Get Windows Intune setup to work with Windows 10 machines”.
Here’s what I found and hopefully this will help others who embark upon this same task.
MDM (Mobile Device Management)
MDM exists in Office 365 and as it suggests is a means to manage Mobile devices. MDM can also be managed from within Intune using a single console for all administrative tasks. In order to enable the latter you need to set the MDM management authority to Intune.

Azure AD Join for Windows 10
The growing capabilities of Windows 10 to utilize Azure cloud services/features are pretty fantastic.
- SSO with all other Office 365 apps
- MDM Enrollment and conditional access for BYOD users
- MFA and Pass Port for work management
Here is a good article detailing features/scenarios and setup: https://blogs.technet.microsoft.com/ad/2015/05/28/azure-ad-join-on-windows-10-devices/
The Interesting Problem…
MDM whether it is managed in Office 365 or Intune recognizes Windows 10 Devices as Mobile devices. The only policies that can then be deployed to these machines is a Mobile Policy vs. a computer policy.
What does this mean?
Plain and simple, as I was told by MS Cloud Services support, if you want to manage Windows 10 in Intune utilizing the Windows Computer policies vs. Mobile then you will need to turn MDM off or provision specific users using a designated Group.
The Proper Way to Set up Intune and Windows 10 Machines
Turn off MDM in Azure AD from the application settings of Microsoft Intune OR create a specific group from which to add only those users whom will require a Mobile device policy. If the setting is configured as ALL then Windows 10 systems will be auto-enrolled in the MDM policy when they join Azure AD.
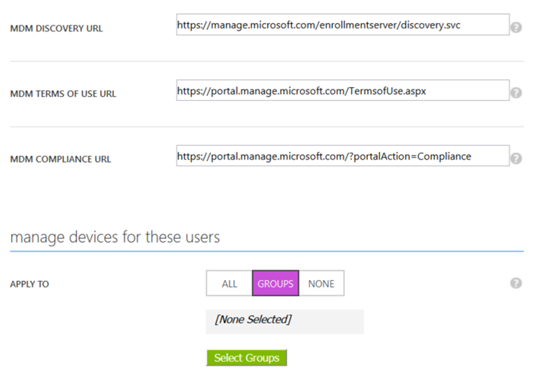
Once the above step has been done have each NON-domain joined Windows 10 machine join Azure AD. On a side note Pass Port for work can be configured in the Intune portal to provide Windows 10 machines with enhanced and granular security features.
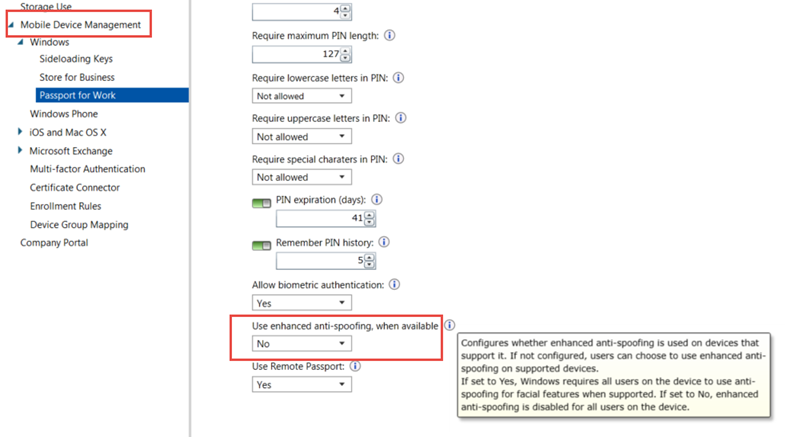
After the Azure Domain join the Intune client can then be installed on the Windows 10 device where the Windows policy can be deployed
Excellent many thanks for your post 🙂
Do i understand correct, that if we want to use the intune client for windows 10 we need to disable MDM?
Wow – thank you! This is the /only/ site that I’ve found which details how to set up Azure and Intune to properly manage Windows10 machines. We were trying all sorts of things, but could not both join AzureAD for corporate Windows log-in and get managed with Intune at the same time – it was always one or the other. As soon as we flipped the MDM setting to ‘Selected Groups’ and put in an empty group, we could magically have AzureAD login and Intune client management. Now if we could just get the Intune Client to install automatically…
Good-article. Thank you!
This will address the issue of enrolling windows 10 laptops but how do you manage the case when users have both laptops and mobile devices?
If they are not part of the group, mobile devices will not enroll and you can not force conditional access…
Amazing. 3 days with MS Support, whose initial reaction said you cannot use the InTune client on a PC and enroll it in Azure AD, and your outline provided the resolution. Thank you.