I ran into the Cerber variant of Ransomware lately and it is nasty. This one is relatively new having surfaced in March 2016, but thankfully I have only seen it once in the wild…so far.
This one is particularly nasty for the following reasons:
-
Runs offline and doesn’t need to be online to fetch encryption keys
-
Encrypted files are fully renamed and given a new file extension
-
Bypasses UAC!
-
Edits some timestamps to blank and user owner making finding the source hard(er)
-
No recovery process other than backups! (so far)
Full detailed write up HERE
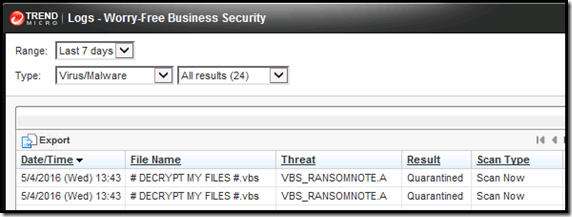
What I experienced was files getting renamed with a .cerber extension, crazy file names and accompanying files with # DECRYPT MY FILES #.html. The user’s desktop got decimated then it started to go to mapped drives even moving to other folders that the user didn’t have mapped on the file share somehow. It weirdly only targeted files that had been modified in the past day. While this kind of makes sense as these would be the files recently used so probably valuable to offer as ransom, but odd as it made it easier to pinpoint files and restore. Since it encrypts the files and completely renames them it does present issues with large amounts of files as finding what is actually gone was tiresome.
***this was my experience and I may of got lucky with it only targeting recent files***
To pinpoint the source we disconnected everyone from the mapped file shares and searched everyone’s local PC’s for *.cerber files. This thankfully only brought up one PC so we threw that one off a bridge.
We then had to restore from backups or from shadow copies if you have them, there is no recovery method other than paying and the FBI does not recommend that.
Trend Micro detects it as below:
Malwareybtes of course also grabs it and they also recommend you use their Antiexplot program HERE. I installed it on PC’s in trial just as a precaution before I let them back onto the network.
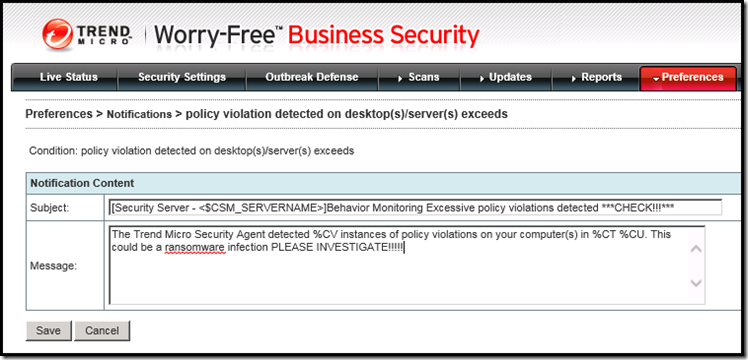
Since we use Trend Micro WFBS at a lot of clients here are a few more tips to cover your bases.
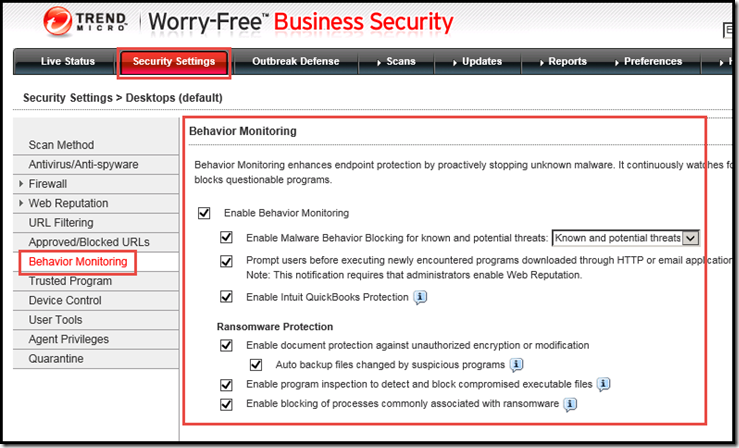
Update Trend WFBS to SP3! SP3 enables the Behavior Monitoring features that protect from Ransomware by default now.
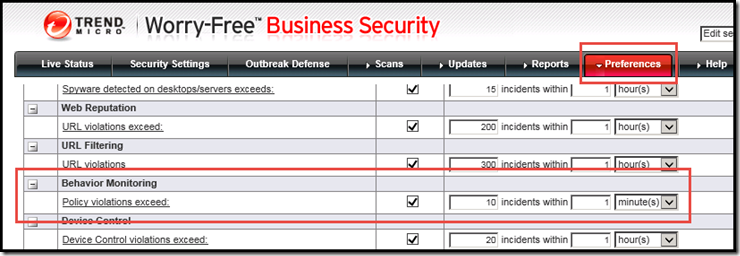
Beef up you notification under Preferences for Behavior Monitoring. Change it to something lower within minutes as Ransomware will infect fast so you want to catch it before it gets too far.
Change the actual alert to be more descriptive and get people’s attention.
Example:
As always there will be lots of different variants so your mileage may vary.
One of my users got this virus. He clicked on an attachment that said it was an invoice. Lucky for us he wasn’t connected to our network so all he lost was the files on his laptop. It did not affect the files in his recycle bin.
I re imaged the machine from the recovery partition. All is back to normal.
I also have WFBS so thanks for info on that.
Hopefully I scared enough people here to be careful on what they click on. But I doubt it.
Thanks for the follow-up, good to know about the invoice attachment. They got something similar, but swear they just deleted it so now I’m not so sure! 🙂