I ran into the stupid CryptoWall Ransomware again it seems. If someone calls and says they are seeing 3 files: DECRYPT_INSTRUCTION.HTML, TXT and a shortcut files this is what to do INSTANTLY.
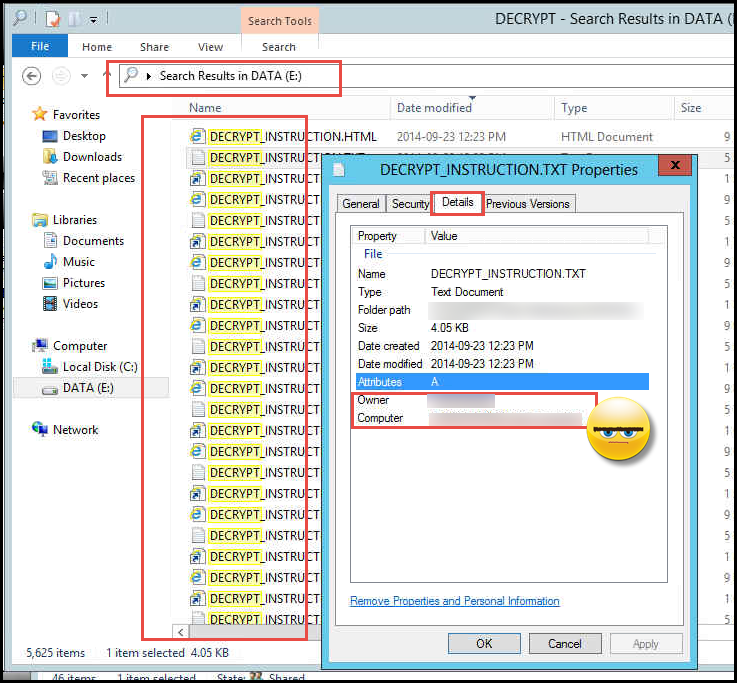
Immediately find one of the DECRYPT_INSTRUCTION.TXT files and right click and go to properties. Then go to Details. FIND the Owner and unplug their machine and throw it in the ocean.
It will first infect the local files and then move onto the network locations they have access to. One way to know if it’s them for sure is if they are the only ones with the DECRYPT files in their “My Documents”, where others will just see it in the network locations. It will also put the files in the users Start-up Folder.
You have now most likely stopped the spread. To find how #$%^ed you are go to the drive or drives and do a full search for DECRYPT_INSTRUCTION. This will tell you what has been encrypted and what you need to restore. You can also try some utilities such as ListCWall to find items LINK. It does about a file a minuet so you can lob it off at the neck if you are fast. You can also from the timestamps pinpoint the exact time within a few minutes from when it struck so you can flog accordingly.
Next restore those files from backup (shadowcopy etc.), you have no other choice unless you want to pay them. Once the files are restored you can use that file search for Decrypt to select all the instruction files and delete them.
For more info on cleanup past running good ole Malwarebytes and CryptoPrevent head on over to HERE.